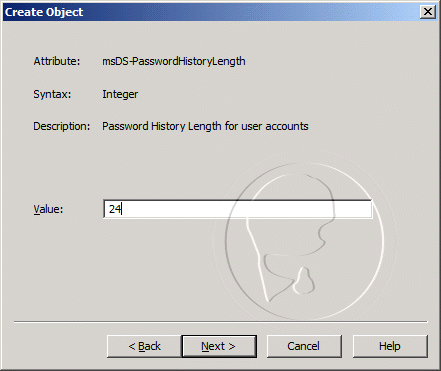
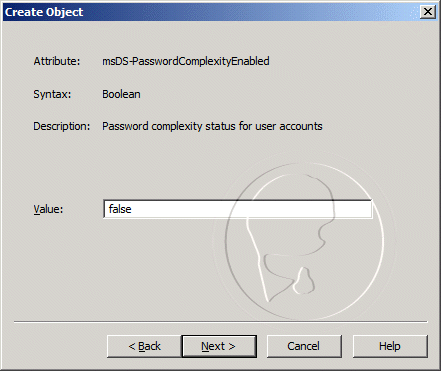
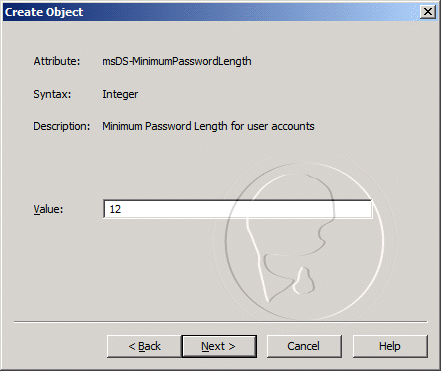
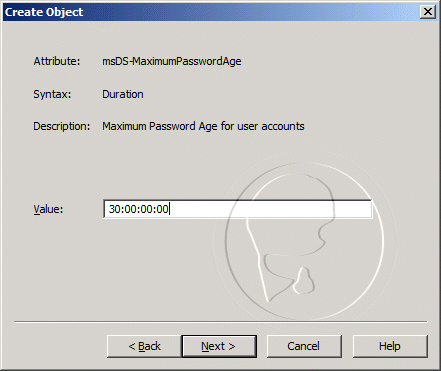
Prerequisites
In order to install SCCM 2007 there are a number of prerequisites that are required to be installed on the machine.
Configuring Internet Information Services on Server 2008R2
On the Windows Server 2008R2 computer, navigate to Start / All Programs / Administrative Tools / Server Manager to start Server Manager. In Server Manager, select the Features node and click Add Features to start the Add Features Wizard.
On the Select Features page of the Add Features Wizard:
Select BITS Server Extensions. When prompted, click Add Required Role Services to add the dependent components, including the Web Server (IIS) role.
Select Remote Differential Compression, and then click Next.
On the Web Server (IIS) page of the Add Features Wizard, click Next.
Click Next on the IIS installation page
Under Application Development, select ASP.NET and, when prompted, click Add Required Role Services to add the dependent components.
Select ASP because the site system will be configured as a reporting point.
Under Security, select Windows Authentication.
In the Management Tools node, under IIS 6 Management Compatibility, ensure that both IIS 6 Metabase Compatibility and IIS 6 WMI Compatibility are selected and then click Next.
Under common http feature ensure that WebDav publishing is installed
Click Next
On the Confirmation page, click Install, and then complete the rest of the wizard.
Click Close to exit the Add Features Wizard, and then close Server Manager.
WebDAV is required to support management point and BITS-enabled distribution point site system computers.
Enable WebDAV and create an Authoring Rule, as follows:
Navigate to Start / All Programs / Administrative Tools / Internet Information Services (IIS) Manager to start Internet Information Services 7 Application Server Manager.
In the Connections pane, expand the Sites node in the navigation tree, and then click Default Web Site if you are using the default Web site for the site system or SMSWEB if you are using a custom Web site for the site system.
In the Features View, double-click WebDAV Authoring Rules.
When the WebDAV Authoring Rules page is displayed, in the Actions pane, click Enable WebDAV.
After WebDAV has been enabled, in the Actions pane, click Add Authoring Rule.
In the Add Authoring Rule dialog box, under Allow access to, click All content.
Under Allow access to this content to, click All users.
Under Permissions, click Read, and then click OK.
Change the property behavior as follows:
In the WebDAV Authoring Rules page, in the Actions pane, click WebDAV Settings.
In the WebDAV Settings page, under Property Behavior, set Allow anonymous property queries to True.
Set Allow Custom Properties to False.
Set Allow property queries with infinite depth to True.
If this is a BITS-enabled distribution point, under WebDAV Behavior, set Allow hidden files to be listed to True.
In the Action pane, click Apply.
Close Internet Information Services (IIS) Manager.
RDC is required for site server and branch distribution point computers
SCCM primary sites must constantly communicate with a Microsoft SQL Server hosting the site database. Typically, performance is better if the SCCM site server and the site database are installed on the same server however, if a high-availability, high-bandwidth connection is present leveraging SQL on a remote server is an option. Since AT run a number of different Beta products we have decided to run a local installation of sql 2008 sp2
1. SQL 2008 requires the installation of .Net 3.51 which can be installed from the features section in server manager. On the Windows Server 2008R2 computer, navigate to Start / All Programs / Administrative Tools / Server Manager to start Server Manager. In Server Manager, select the Features node and click Add Features to start the Add Features Wizard.
2. On the Select Features page of the Add Features Wizard and select .Net Framework 3.5.1
3. On the Add feature popup select add required features
4. Click Install
5. Insert the SQL Server 2008 CD and click on Install Server Components, if the splash screen does not appear, run Splash.hta from the .\Servers directory.
6. After launching the Sql 2008 setup select installation from the left menu
7. Select New SQL Server stand-alone installation
8. Click OK on the setup support rules
9. Enter the product key and select Next
10. Click I Accept the license terms and then click Next
11. Click Install on the Setup Support files page
12. Click Next on the Setup Support Rules page
13. On the feature selection page select the following: Database Engine, Full Text Search, Reporting Services, Management Tools Complete
14. We will be installing our SQL information to the D: drive and click Next
15. Accept the defaults on the instance configuration page (validate D: drive for the root directory) and click Next
16. Select Next on the disk space requirements page
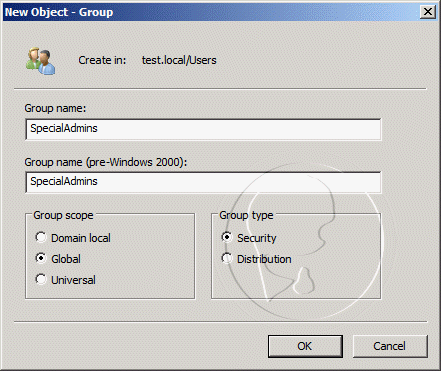
17. On the server configuration page enter the Service account that we previously created (see table1)
18. On the Database Engine configuration leave Windows Integrated and add the appropriate account for SQL Admin and click NEXT
19. On the Reporting Services Configuration leave the default of Install Native Mode default configuration
20. On the Error Reporting page accept the defaults and click NEXT
21. Make sure all the rule have passed then click NEXT
22. Click INSTALL on the Ready To Install page
23. On the Install Progress page click NEXT
24. Click CLOSE on the completion page
Installing SQL 2008 SP1
1. Double click the SQL SP1 installation file En_SQL_Server_2008_SP1_x64.exe
2. On the Welcome screen click NEXT
3. Accept the License terms and click NEXT
4. on the Selection Features click NEXT
5. On the Check files in Use page click NEXT
6. Click UPDATE on the Ready to update screen
7. On the update progress page click NEXT
8. Click CLOSE on the completion page
Leveraging a remote SQL instance
When installing the site database on a remote SQL Server computer, the logged on user and site server machine account require administrative rights to the remote SQL Server computer. If installing the site database on a SQL Server cluster instance, the logged on user and site server machine account require administrative rights to all SQL Server cluster instance node computers.
The TCP/IP protocol is required for SQL Server network communications to allow Kerberos authentication. The named pipes protocol is not required for SCCM site database operations and should only be used to troubleshoot any Kerberos authentication issues encountered when using TCP/IP protocol communication. By default, SQL Server uses TCP port 1433 to listen on TCP/IP. To change the port, or network communication protocol used, start the SQL Server Configuration Manager, and click Protocols for .
Configuration Manager 2007 Setup automatically creates the site database, using SQL Server defaults, on the SQL Server computer and instance specified during setup. If the configured SQL Server default settings are not sufficient to manage your site database, it is recommended that you pre-create the database and set the required settings. If you are using a remote SQL Server to host the site database, you should ensure that the site server’s computer account has sufficient privileges on the SQL Server computer to create the site database before beginning the installation process.
If you configure a domain user account to run the SQL Server service instead of the local system account a Service Principal Name (“SPN”) must be configured for the domain user account in Active Directory Domain Services.
Click Start, click Run and then enter CMD in the Run dialog box.
Enter a valid command to create the SPN. The command should be in the form of:
setspn –A MSSQLSvc/:1433
Verify that the command completed successfully by reviewing the command’s output for the updated object line
Click Start, click Run, and enter adsiedit.msc to launch the ADSIEdit MMC console, connect to the domain
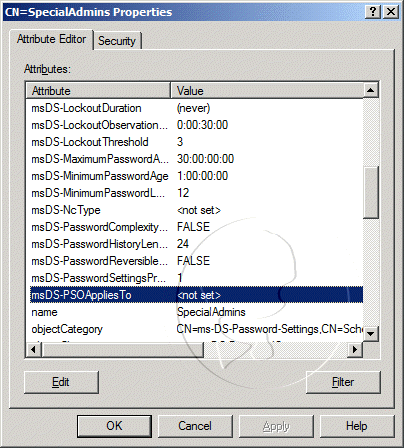
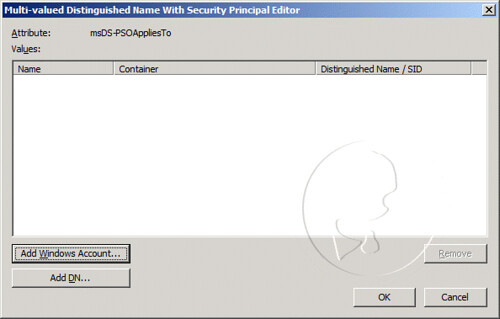
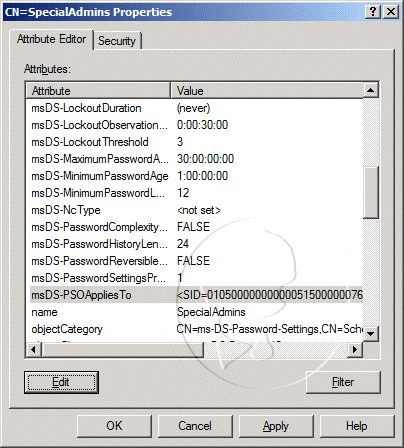
In the console pane, expand the domain, expand DC=, expand CN=Users, and right-click CN=. On the context menu, click Properties
In the CN= Properties dialog box, review the ServicePrincipalName value to ensure that a valid SPN has been created and associated with the correct SQL Server
The following section outlines the installation process to install the core SCCM software, additional site system roles and, supporting components.
Create a backup of the schema master domain controller’s system state using the standard CompanyX backup process.
Log on to the schema master domain controller with an account that is a member of the Schema Admins security group.
Disconnect the schema master domain controller from the network.
Click Start, click Run, and enter adsiedit.msc to launch the ADSIEdit MMC console , connect to the domain.
In the console pane, expand Domain, expand the distinguished name entry, and right-click CN=System.
On the context menu, click New and then click Object.
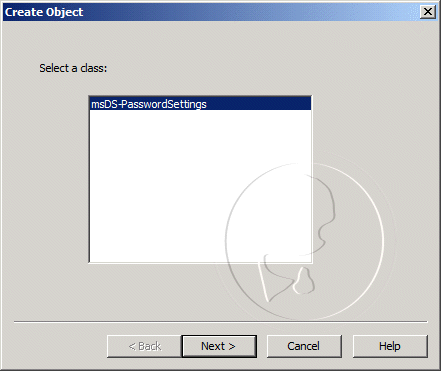
In the Create Object dialog box, select Container and click Next.
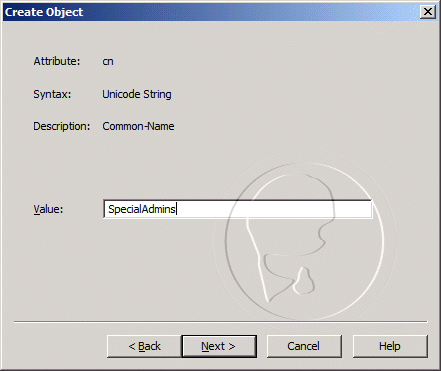
In the Value field, type System Management and click Next.
Click Finish and close the ADSIEdit MMC console.
Click Start, Click Run, and enter dsa.msc to open the Active Directory Users and Computers administrative tool.
Click View, and then click Advanced Features.
In the console pane, expand the System container.
Right Click the System Management container and select Properties
In the Security tab click the Add button
Click the Object Types button and select Computers
In the Object Names field enter the SCCM server’s machine account e.g.$, click OK
In the Security tab select the machine account then click the Advanced button
Select the machine account in the Permissions window and click the Edit button
In the Apply to: field select “This object and all descendant objects” and select Full Control under permissions
Close the Active Directory Users and Computers administrative tool
Run extadsch.exe, located at \SMSSETUP\BIN\I386 on the SCCM installation media, to add the new classes and attributes to the Active Directory schema.
Verify that the schema extension was successful by reviewing the extadsch.log located in the root of the system drive.
If the schema extension procedure was successful, reconnect the schema master domain controller to the network and allow it to replicate the schema extensions to the global catalog servers throughout the Active Directory forest.
If the schema extension procedure was unsuccessful, restore the schema master’s previous system state from the backup created in step 1. This will reverse the schema extension actions before reconnecting the schema master domain controller to the network.
Create a directory to hold updated installation files at C:\Install Source\Updates
Execute SPLASH.HTA, from the root of the SCCM installation media to start the setup wizard.
Click Run the Prerequisite Checker
Input the SQL Server Name, SDK Server , and Management Point server and click OK
You see we have a warning related to WSUS, however since we are not integrating that component at this time we can click OK
Launch Setup
Click Install Configuration Manager SP2
Click Next on the Welcome page.
On the Available Setup Options page, select the Install a Configuration Manager Site Server option.
Agree to the licensing terms on the License Agreement page, click Next.
On the Installation Settings page, select the Custom Settings option.
On the Site Type page, select Primary site.
On the Customer Experience Improvement Program page, select “No, I do not want to participate right now”.
On the Configuration Manager Product Key page, The AT key is entered by default.
On the Destination Folder page, enter d:\Program Files (x86)\Microsoft Configuration Manager\
On the Site Settings page, enter a three letter site code in the Site Code field and AT Belvoir Site in the Site Name field.
On the Configuration Manager Site Mode page, select Configuration Manager in Mixed Mode.
On the Configuration Manager Client Agents page, select all the client agents but Network Access Protection to enable them with their default settings.
On the Configuration Manager Database Server page, enter the Microsoft SQL Server NetBIOS name, , and the SQL 2008 database name, SMS_ABV
On the SMS Provider Settings page, enter the NetBIOS name of the local server to install the SMS Provider on, .
On the Configuration Manager Management Point page, choose to install a management point during setup. Verify the NetBIOS name of the server, , is targeted to install the management point site system role.
On the Configuration Manager Port Settings page, accept the default port (80) to be used for client-to-site-system communications.
On the Updated Prerequisite Components page, select “Check for new updates and download them to an alternate path”.
Enter C:\Install Source\Updates for the alternative path to store the updates.
Note: The Setup command line option Setup /download can be used to download client prerequisite component files without running the complete Configuration Manager Setup wizard.
On the Settings Summary page, review the summary details for the site installation before continuing.
When prerequisite checking has completed, review any messages in the results pane of the Prerequisite Check page to verify that all prerequisites have been met or that Configuration Manager Setup can resolve any prerequisites that have not been met for installation to continue.
Review the installation steps on the Installation Status to verify the actions taken and their status as Configuration Manager is installing. Clear the checkbox to Launch the Configuration Manager console after closing.
The Completion page displays whether or not the installation was successful and the details of the primary site installation as well as the options to view the setup log file (ConfigMgrSetup.log) and launch the Configuration Manager console.
After installing the SCCM Central Site, additional site system roles are required to support ABM functional requirements.
A MP is required to transfer information between SCCM clients and SCCM servers, without a functional MP, clients cannot be managed.
In the Configuration Manager console, navigate to System Center Configuration Manager / Site Database / Site Management / YourSite / Site Settings / Component Configuration.
Right-click Management Point, and then click Properties.
If the default management point for the site will be a standard site system, click Management Point, and then select an available management point site system from the Server name list.
If the default management point for the site will be an NLB clustered management point, click Network Load Balancing cluster virtual server and configure the IP Address or FQDN information for the NLB cluster configuration.
Click OK to save configuration changes and close the management point properties.
Server locator points (“SLP”) are used to complete client site assignment on the intranet and help clients find management points when they cannot find that information through AD. Clients must use a server locator point if the AD schema is not extended for SCCM, the site is not published to AD, or if clients do not belong to the same AD forest as the site server’s forest. The SLP role will not be implemented initially but this section is included to account for potential ABM SCCM environmental for growth.
In the Configuration Manager console, navigate to System Center Configuration Manager / Site Database / Site Management / ABV- AT Belvoir Site / Site Settings / Site Systems.
To create a new site system server and add the reporting point site role: Right-click \\, click New Roles.
Verify the general site system settings for the site system server.
Specify a fully qualified domain name (FQDN) for this site system on the intranet:.
Check: Use the site servers computer account to install this system
Click Next.
Select Server locator point, and then click Next.
Select Use the site database and Use the server locator point’s computer account options then click next
Click Next on the summary page, and then click Close.
Repeat the steps above to validate the following roles are installed and configured
Adding the SLP to Wins is only required if you have non AD joined machines that you want to be managed by SCCM or you plan to manage systems in remote directories.
*This task should be run from a Server that has the Wins Role installed*
Click Start, click Run, type cmd in the Run Dialog Box and then click OK.
At the command prompt, type netsh, and then press Enter.
Type wins, and then press Enter.
Type server, and then press Enter. To manage a remote WINS server, type server\\.
Type the appropriate command, as in the following example: add name Name=SMS_SLP endchar=1A rectype=0 ip={SERVER IP address here}
Click Start, click Run, enter cmd in the Run dialog box and then click OK.
At the command prompt, type netsh, and then press Enter.
Type wins, and then press Enter.
Type server, and then press Enter. To manage a remote WINS server, type server \\.
Type the following command: show name Name=SMS_SLP endchar=1A.