This step-by-step guide provides instructions for configuring, applying and editing fine-grained password and account lockout policies for different sets of users in Windows Server 2008.
In Microsoft Windows 2000 and Windows Server 2003 Active Directory domains, you could apply only one password and account lockout policy, which is specified in the domain's Default Domain Policy, to all users in the domain. As a result, if you wanted different password and account lockout settings for different sets of users, you had to either create a password filter or deploy multiple domains.
Fine-Grained Passwords in Windows Server 2008
In Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain. For example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and then apply less strict settings to the accounts of other users.
Another valid application for using fine-grained password policies, are situations where legacy applications or other data sources require password synchronization. These situations may require us to relax certain aspects of password complexity or length.
Step-By-Step Configuration of Fine-Grained Passwords in Windows Server 2008
I find it’s best to work with an example to demonstrate a solution, so in this case we will assume that you have a number of users who are Special Administrators and require a stronger password group policy than the standard user. We will refer to these users as SpecialAdmins
In the following steps, we will configure a fine-grained password policy in Windows Server 2008 with the following settings:
| Policy Name | Policy Setting |
Enforce password history | 24 passwords remembered |
Maximum password age | 30 days |
Minimum password age | 1 day |
Minimum password length | 12 characters |
Passwords must meet complexity requirements | Disabled |
Account lockout duration | 0 |
Account lockout threshold | 3 |
Reset account lockout counter after | 30 minutes |
Table 1: Password Policy
Note: yourdomainname in the following steps should be replaced with the NETBIOS name of your domain.
- Logon to a Windows Server 2008 domain controller using an account that has membership in the Domain Admins group, or equivalent permissions.
- Go to Start, Administrative Tools, and then select Active Directory Users and Computers
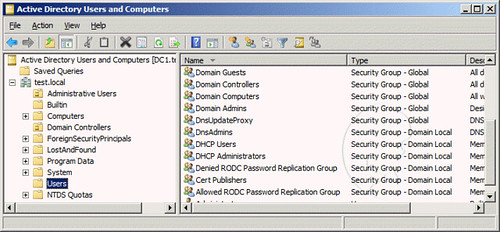
- Expand yourdomainname.com, right-click on the Users container, select New, and then select Group.
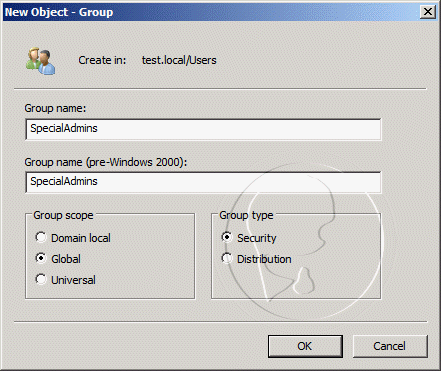
- On the New Object - Group window, enter SpecialAdmins into the Group Name field, and then click OK
- Close Active Directory Users and Computers
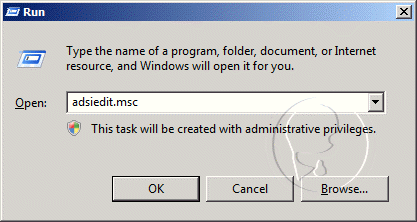
- Click Start, click RUN, type ADSIEDIT.MSC, and then click OK
- In the ADSI Edit snap-in, right-click ADSI Edit, and then click Connect to
- In the Name field, enter yourdomainname.com, and then click OK
- Double-click yourdomainname.com in the console tree, double-clickDC=yourdomainname,DC=com, double-click CN=System, and then click CN=Password Settings Container
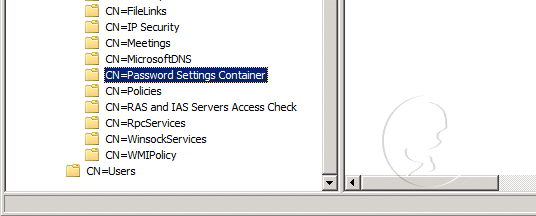
- Right-click CN=Password Settings Container in the console tree, click New, and then clickObject
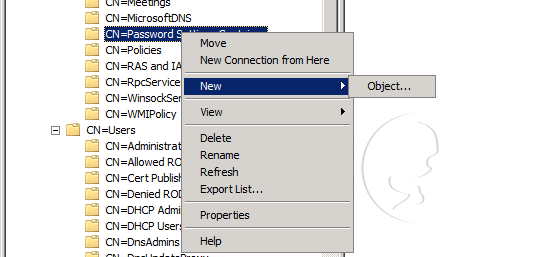
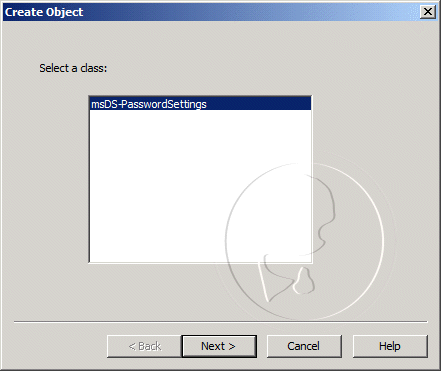
- In the Create Object dialog box, under Select a class, click msDC-PasswordSettings, and then click Next.
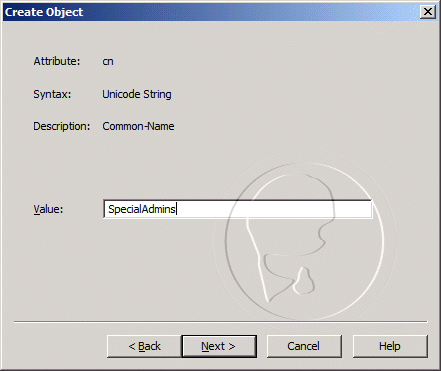
- In the Create Object dialog box, enter SpecialAdmins in the Value field, and then clickNext.
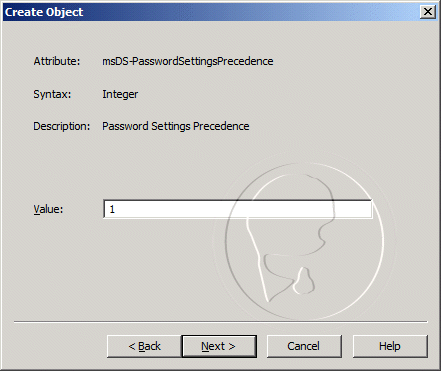
- For the msDS-PasswordSettingsPrecedence value, enter 1, and then click Next
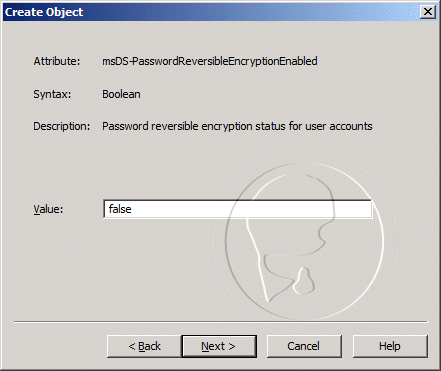
- For the msDS-PasswordReversibleEncryptionEnabled value, enter false, and then clickNext
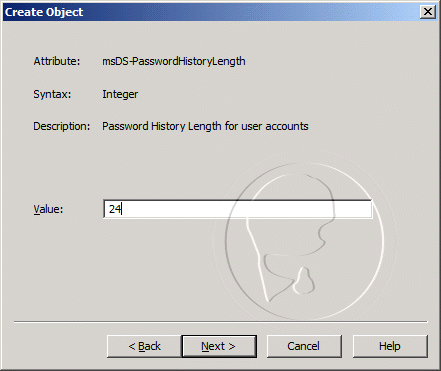
- For the msDS-PasswordHistoryLength value, enter 24, and then click Next
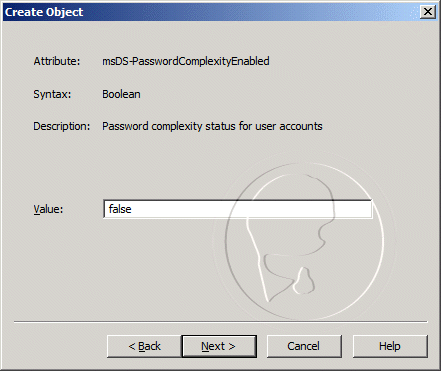
- For the msDS-PasswordComplexityEnabled value, enter false, and then click Next
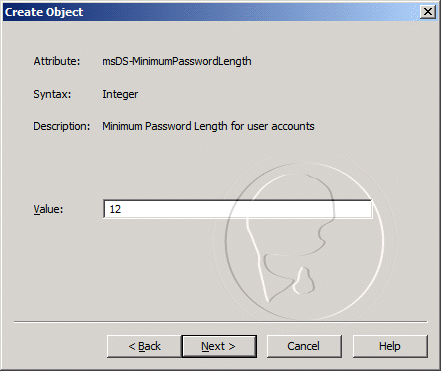
- For the msDS-MinimumPasswordLength value, enter 12, and then click Next
- For the msDS-MinimumPasswordAge, enter 1:00:00:00, and then click Next

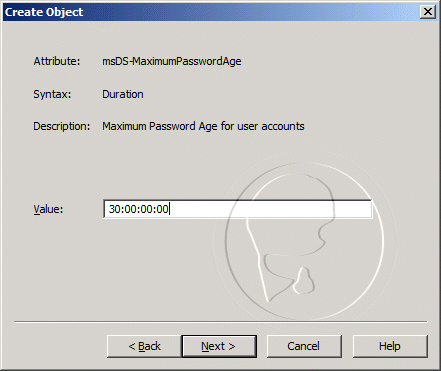
- For the msDS-MaximumPasswordAge, enter 30:00:00:00, and then click Next
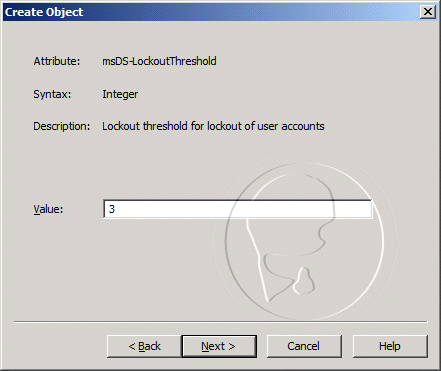
- For the msDS-LockoutThreshold, enter 3, and then click Next
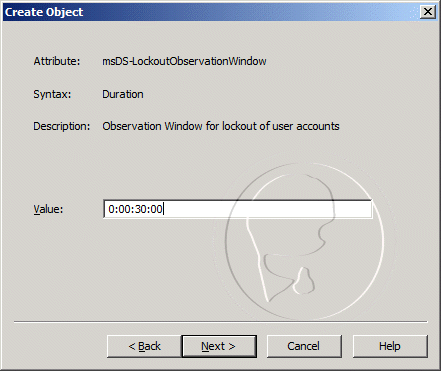
- For the msDS-LockoutObservationWindow, enter 0:00:30:00, and then click Next
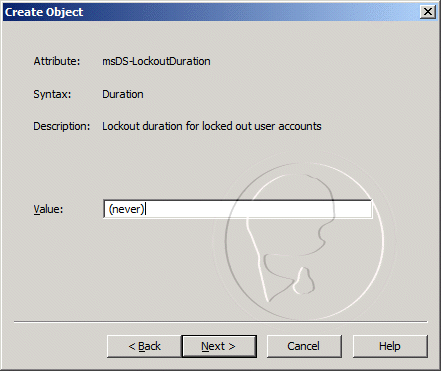
- For the msDS-LockoutDuration, enter (never), and then click Next, then click Finish
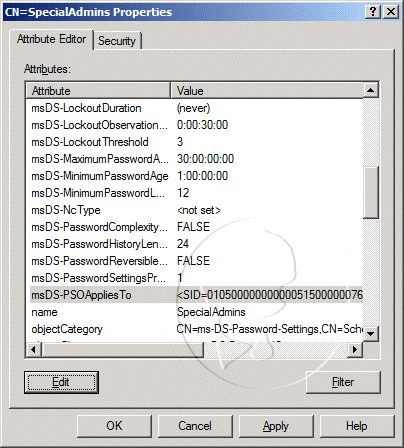
- Right-click on CN=SpecialAdmins in the console tree, and then select Properties
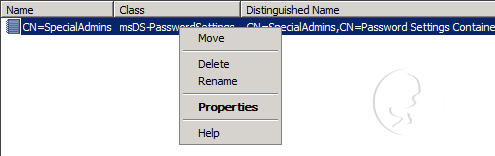
- On the CN=SpecialAdmins Properties window, select the msDS-PSOAppliesTo attribute, and then click the Edit button
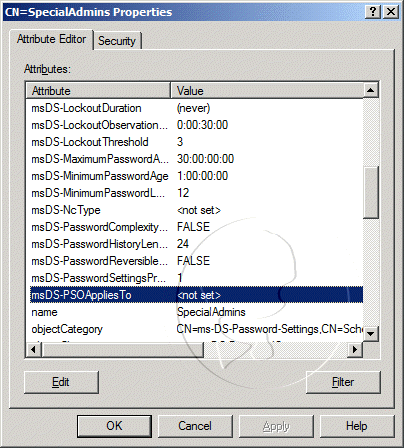
- On the Multi-valued Distinguished Name With Security Principal Editor window, click on the Add Windows Account button
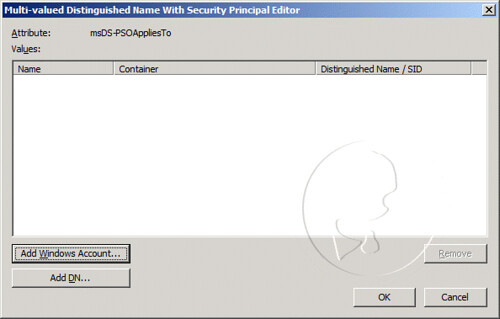
- On the Select Users, Computers, or Groups window, enter SpecialAdmins in the Enter the object names to select field, and then click OK
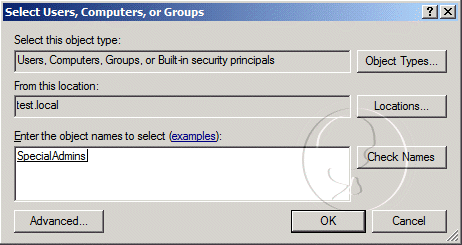
- Click OK on the Multi-valued Distinguished Name With Security Principal Editor window
- Click OK on the CN=SpecialAdmins Properties window
Conclusion
This step-by-step guide demonstrated how to configure fine-grained passwords in WindowsServer 2008. We defined a number of password settings and applied it to a Active Directory Group. From now on, all user members of the group will be applied with the custom password policy.
References
What is the function of the msDS-LockoutDuration element of the fine-grain account lockout policy?
http://www.ucertify.com/article/what-is-the-function-of-the-msds-lockoutduration-element-of-the-fine-grain-account-lockout-policy.html
http://www.ucertify.com/article/what-is-the-function-of-the-msds-lockoutduration-element-of-the-fine-grain-account-lockout-policy.html
AD DS Fine-Grained Password and Account Lockout Policy
http://technet.microsoft.com/en-us/library/cc770842.aspx
http://technet.microsoft.com/en-us/library/cc770842.aspx
Active Directory Domain Services
http://technet.microsoft.com/en-us/library/cc770357.aspx
http://technet.microsoft.com/en-us/library/cc770357.aspx
Windows Domain Password Policies
http://technet.microsoft.com/en-us/magazine/cc137749.aspx
http://technet.microsoft.com/en-us/magazine/cc137749.aspx
Keine Kommentare:
Kommentar veröffentlichen