Microsoft chose moving to secure messaging and secure service access since Exchange Server 2007. The only troublesome task for administrators was to manage these certificates. Folks who are highly addicted to GUI found it little hectic. Good news for those who don’t want to take too many efforts and would like to have a graphical interface that can manage certificates for exchange!
Though not with exchange 2007, Exchange 2010 Beta offers some extended functionality of creating, removing and managing certificates using GUI.
To create a new certificate you can choose the following options;
1. Select Server Configuration from left hand side pane in EMC and Exchange Certificates tab in left hand pane.
2. Right click in free space in left hand side pane of Exchange Certificates tab and select New Exchange Certificate
3. Selecting New Exchange Certificate from the context menu will bring up the introduction screen.
Here at this screen you are prompted to enter a friendly name for the certificate that will appear in EMC as a primary reference for management of certificates if you have multiple certificates created for multiple websites.
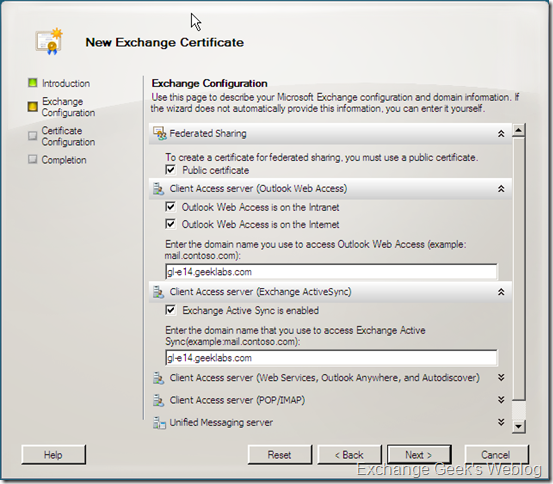
4. Once you have specified a friendly name for the certificate you are taken to the next screen upon clicking the Next button. This New Exchange Certificate screen will now gather the actual required information where you get a chance to choose among the options to use this certificate for various services.
Services like IIS based web services including Autodiscover, OWA EAS and other services like POP/IMAP, Outlook Anywhere and UM.
You can observe the screenshot below and notice that you get an option to write the URL of the service locations for OWA, EAS, Federated Services, SMTP transport, Etc. These URLs will be used in the certificate request which will be further used to write the SAN certificate information.
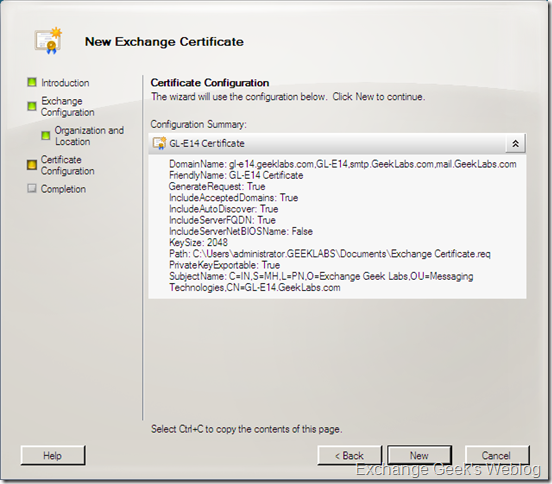
5. here the wizard collects the Organization related information like company name, department, location, etc. At this stage the wizard has collected almost all the information it needed. You may notice that the path right beside the Browse button is the path to the certificate request file path.
6. Next screen summarizes the information you entered.
7. And there you go with the final screen of the wizard where it displays the powershell command it will be attempting to generate the certificate request. Once you hit the Finish button the wizard completes the certificate request.
8. Here a point to be noted is; the wizard does not create an actual certificate. It will simply generate the request and keep it accessible via EMC. So when you are done with the wizard you have to manually send this request to the online CA within your Exchange/AD premises.
Limitations of New Exchange Certificate Wizard:
- The new Exchange Certificate Wizard does not send the request to the online CA directly unless you manually complete the pending request.
- Renewals of expired certificates can not be done using Exchange Certificate Wizard. You still have to user EMS for renewal of certificates.
- New certificates created using New Exchange Certificate Wizard does not get assigned to IIS directly though you do specify the certificate utilization for Exchange Web Services and other IIS integrated exchange services. (You may refer Permanent Link to How to renew a self signed certificate in Exchange Server 2007 for renewal of certificates)
This is the second part of the blog entry Exchange 2010 EMC and Certificate Management in the previous post I wrote about creating a certificate request and the limitations of the new certificate request wizard. In this part we will be looking at obtaining a new certificate and then installing it on the server.
To complete installing a new certificate on your Exchange Server 2010 server you first need to obtain a certificate from CA within your organization or from a third party CA. As stated in last post the New certificate wizard generates a request in a .req file.
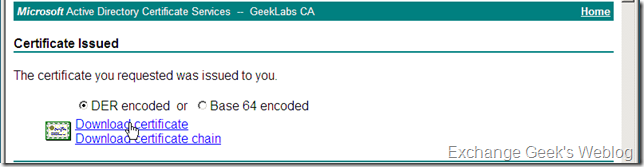
1. To obtain a certificate from a third party CA or your internal CA, your first need to copy the contents of the .req file and paste it to the web console of your certification authority. For my internal Enterprise CA the picture looked like below. Please see carefully that the Certificate Template used for this certificate request is Web Server.
2. Once you are done with above interface by pasting the contents of .req file and choosing a correct template you will be presented with another page in your browser to download the certificate. This interface may vary depending upon the configuration of your CA. You may need to wait till the certificate is approved and issued by CA administrator if configured so. You can now download the certificate in DER encoded format or Base 64 encoded format and save it to some location on your desktop or server. You will also need to download the whole certificate chain if the issuing authority is not a trusted CA by your server.
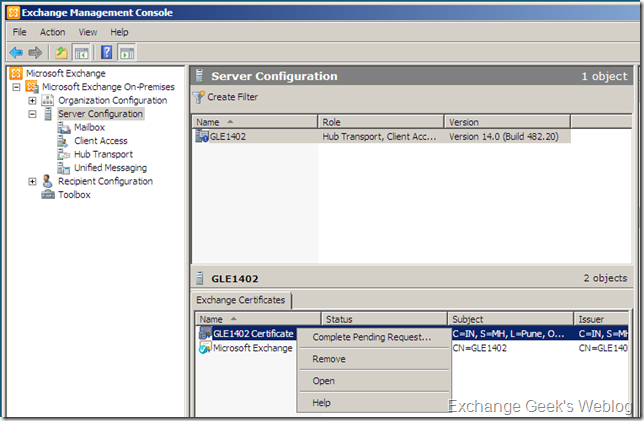
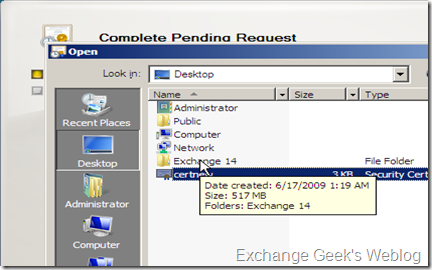
3. Now, as you have downloaded the certificate to the server. You will need to complete the pending certificate request in your EMC. Select the complete pending request by right clicking on the pending certificate request in EMC.
4. A new interface asking you the path to the certificate will pop up. This wizards will ask the location for newly downloaded certificate. Click on the Browse button, select the newly downloaded .cer file and click on complete button.
5. You may recall, Exchange 2007 to have the imported certificate to be enabled before it can be used actually used exchange services. E14 is not an exception to it but you don’t need to use Enable-ExchangeCertificate this time. You can do it using GUI easily. Now that you know, you have a new certificate imported correctly. You need to assign it to the services those will be using it.
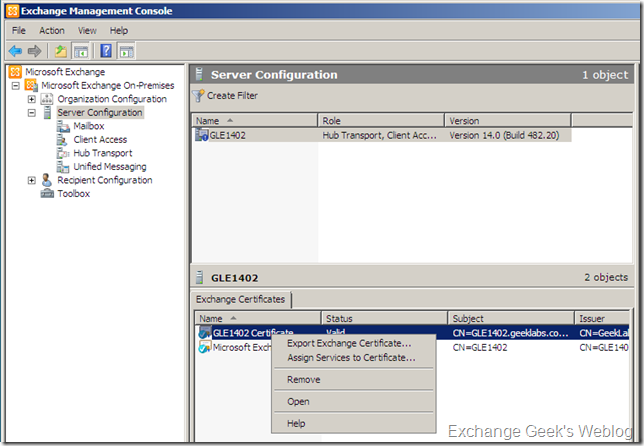
Again, locate the new imported certificate in EMC and right click on it. Select Assign Services to Certificate… from the context menu.
One quick difference you may notice between the step 3 and now. That is the certificate status. It changes from Pending to Valid and icon in front of the certificate gets blue colored check mark on it.
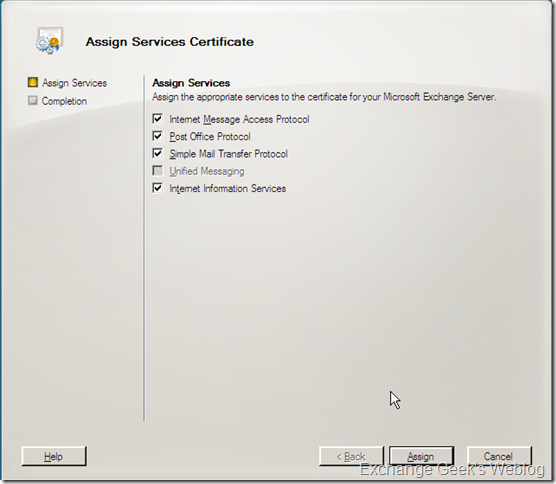
6. Assign Services to Certificate… will list the services on a window those will be assigned to use this certificate. Select the services you want to use this certificate with and click on Assign button. In my case I did not have the UM role installed on the server so the Unified Messaging check box is grayed out.
7. You may notice a pop up asking your consent to assign this certificate to SMTP service on the server as the default certificate will be replaced if you have selected Simple Mail Transport Protocol to use the new certificate in step 6. Click Yes and your default self signed certificate created and assigned to SMTP during server install will be replaced with new one.
Click Finish in the wizard and you are done.
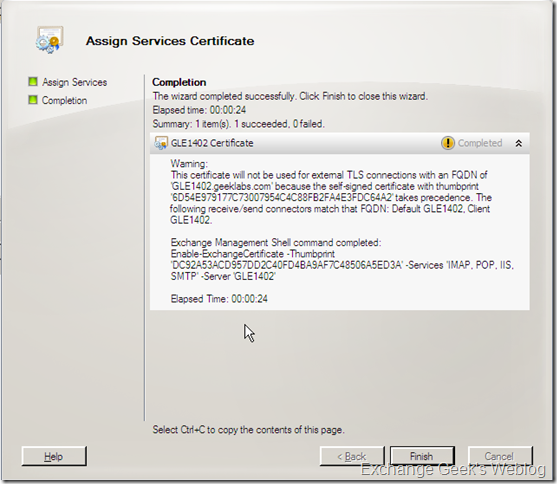
In some cases you may end up with a warning message; warning you that this certificate will not be used for TLS connections. Something like below:
Here you need to really understand the configurations you choose at the time of new certificate request. If you want to use this new certificate for a connector which provides a TLS connections, you will have to mention that during the New Certificate Request Wizard.
Few things to note:
- You must make sure that you have chosen the option to use new certificate for TLS connections during the request generation.
- You must have the root CA and the entire certificate chain installed your Exchange Server as well as clients if you are using your internal CA for new request processing. Outlook as well as Outlook Anywhere and other web based services may be affected otherwise.
- You must back up the certificate as soon as it is enabled on the server. I will write about it in Part-3 of this series.
- I recommend backing up and removing any old certificate from the server as soon as the new certificate is active and fully functional.








AntwortenLöschenSuper Bowl
Super Bowl Live
Super Bowl Live Stream
Super Bowl Live Online
Watch Super Bowl
Super Bowl LII
Super Bowl 2018
Super Bowl 2018 Live
Super Bowl 2018 Live Stream
Watch Super Bowl 2018
2018 Super Bowl
Super Bowl 52
Super Bowl 2018 Score
Super Bowl 2018 TV channel
AntwortenLöschenSuper Bowl 52
Super Bowl 52 Live
Super Bowl 52 Live Stream
Watch Super Bowl 52
Super Bowl
Super Bowl Live
Super Bowl 2018
Super Bowl
Super Bowl Live
Super Bowl 2018
Super Bowl 2018 Live
Super Bowl 2018 Live Stream
2018 Super Bowl
Super Bowl LII
State of Origin
AntwortenLöschenState of Origin Live
State of Origin 2019
State of Origin 2019 Live
State of Origin series
State of Origin
State of Origin Live
State of Origin 2019
State of Origin 2019 Live
State of Origin series
AntwortenLöschenFury vs Schwarz
Fury vs Schwarz Live
Fury vs Schwarz Fight
Schwarz vs Fury
Tyson Fury vs Tom Schwarz
Fury vs Schwarz
Fury vs Schwarz Live
Fury vs Schwarz Fight
Schwarz vs Fury
Tyson Fury vs Tom Schwarz
India vs Pakistan
India vs Pakistan Live
India vs Pakistan Cricket
Pakistan vs India
Pakistan vs India Live
India vs Pakistan
Pakistan vs India
India vs Pakistan
Pakistan vs India
US Open
US Open Golf
US Open 2019
US Open Golf 2019
AntwortenLöschenFrench Grand Prix
French Grand Prix Live
French Grand Prix 2019
French Grand Prix 2019 Live
F1 French Grand Prix
Formula 1 French Grand Prix
French Grand Prix
French Grand Prix Live
F1 French Grand Prix
Formula 1 French Grand Prix