SSL Client Certificate Authentication allows users authenticate to TMG using smart cards. This post explains how to configure TMG and Active Directory for certificate authentication.
In my previous article I explained the use of one-time passwords with Forefront Threat Management Gateway (TMG). Today, I will discuss an alternative to this method that leverages smart cards and Public Key Infrastructure (PKI). I will describe how to use certificates that are published on the TMG.
For this to work, you don’t’ have to deploy an Enterprise Certification Authority. You can use any certificate issued by a public or private CA. Two things are required for this:
- The CA that issued the user certificate has to be added to the Certificate trust list (CTL) on the TMG Listener
- The user certificate has to be mapped to the user’s Active Directory credentials
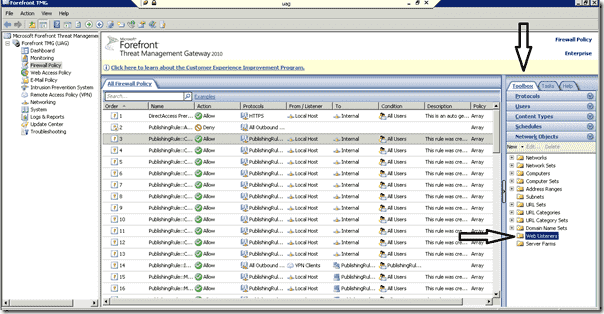
TMG Web Listener
Next, click the Toolbox tab, and then Network Objects.
Now, right click on the listener that you created before and select the “Authentication” tab.

SSL Client Certificate Authentication
Select “SSL Client Certificate Authentication” from the dropdown menu. You can only choose “Windows Active Directory” to validate the credentials.
Click on “Advanced”, and then select the Client Certificate Trust list. You have two options here:

SSL Client Certificate Authentication – Advanced Authentication Options
You can either allow certificates from all issuers that are trusted on the TMG, or select only specific trusted certificates. I suggest accepting certificates only from those CAs that your users will actually use. If you want to accept certificates from a public CA that is not in the Trust List, you must also add the CA Root certificate to the TMG.
You can map a certificate to a user account using Active Directory, but first you need the user’s exported public key. Open Active Directory Users and Computers, select “View” and click on “Advanced Features”.
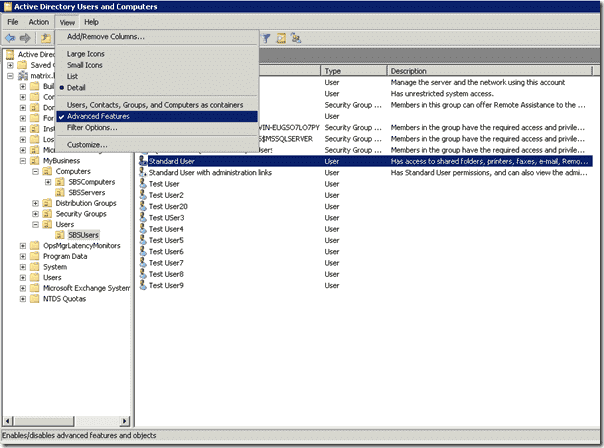
SSL Client Certificate Authentication – Active Directory Advanced Features
Now, navigate to the user account, right click the user name and select “Name Mappings”,
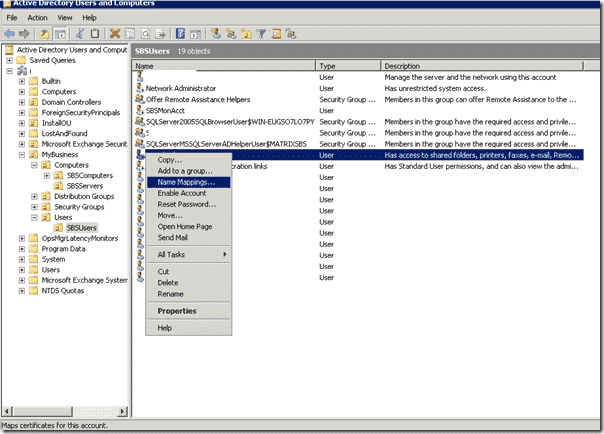
SSL Client Certificate Authentication – Name Mappings
Click “Add” and point to the CER file that contains the user’s public key. This user can now be authenticated on the TMG Listener.
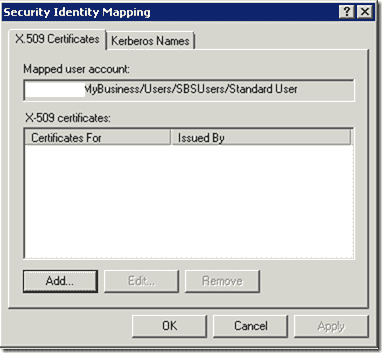
SSL Client Certificate Authentication – Security Identity Mapping
Do not confuse this method with smart card authentication on workstations; you will still require specific certificates for smart card logins. I strongly recommend that you allow only user certificates that are stored on smart cards. As far as I know, this can’t be enforced on the TMG.
When a user accesses Outlook Web Access (OWA), he will be asked to provide a certificate and a smart card PIN. Once he authenticated successfully to the TMG, he will be automatically logged on to OWA.
Keine Kommentare:
Kommentar veröffentlichen